
Our team of security experts can design solutions for you.

Easy of Use
DIAGNOSTIC TOOLS
Reliability, log audit
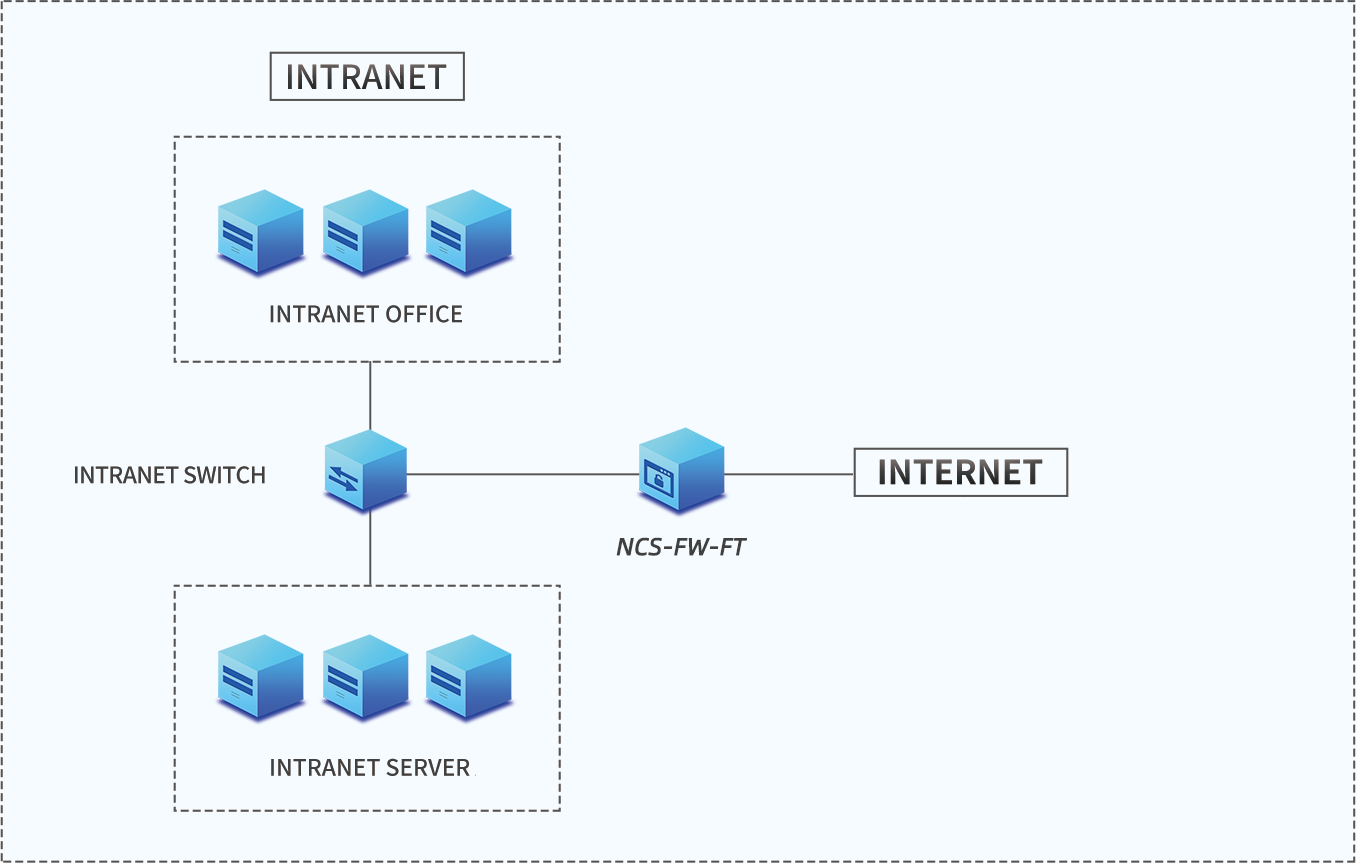
The product focuses on network boundaries and provides L2-L7 layer protection. It can be used in application scenarios such as Internet exits and security area boundary protection, improving network security protection capabilities and helping users cope with increasingly complex security threats.